Virtualbox 32 Bit - downyup. VirtualBox for Windows 7 - original software that allows you to experiment with operating systems. Creates a virtual machine, allows you to set iron parameters within certain limits. The advantage is the modular architecture and the presence of internal logic. Suitable for users with an average level of skills. If you already have VirtualBox or VMware installed, then this is probably the fastest/easiest was to get Kali Linux running. Both 32-bit and 64-bit images are available on the Kali Linux Custom. There are two ways to install Kali Linux on VirtualBox: 1. Download and import the kali Linux VirtualBox image provided by kali itself. (Quickest way) 2. Manually install Kali Linux on virtualbox using the ISO file. The first way to import kali Linux image on VirtualBox has been covered in my “setup a pen-testing lab” post. Sha256sum kali-linux-2018.1-vbox-i386.ova”-If the checksums dont match, its a bad image and you can re-download. If it does match, check the following:-Are you able to boot other linux 32-bit ova images(for ex: linux mint 32bit) into virtualbox on your MAC?
- Download Kali Iso For Vmware
- Download Kali Linux For Virtualbox 32 Bit For Windows 7 Free Download
- Kali Linux Download For Vmware Workstation
- Download Kali Linux For Virtualbox 32 Bit Download
- Kali Linux Vmware
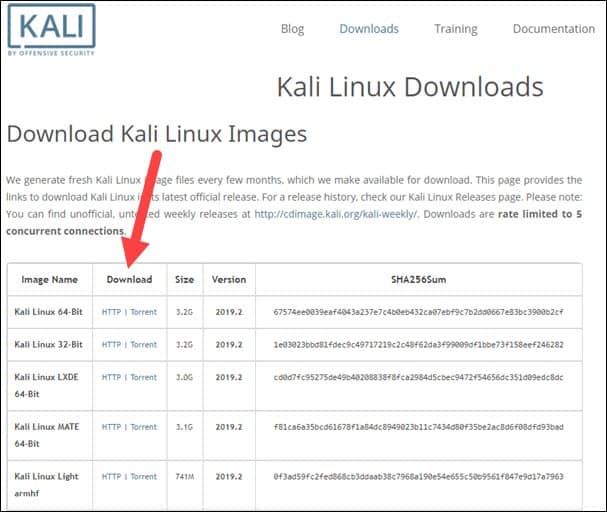
Kali is a rolling Linux distribution, meaning as soon as we have an update, we ship it. Would-be users have a variety of images to choose from. For more information, please see Which Image Should I Download? and Kali Branches. For most users, we recommend the latest “point release” image below, except in cases when a user requires a specific bug patch, in which case the weekly build may be best.
We generate fresh Kali Linux image files every quarter. These become the official 'point' releases. These images are tested and subsequently announced with a blog post.
Installation DocumentationOur previous Kali Linux's releases.
Kali Linux 2021.3 Changelog
SHA256sum
c530562bedcf833e1c981a0e59ed8a5d559628287c1102a9d7d3db86516f9935Weekly
Untested images with the latest updates
SHA256sum
3a199fce1220a09756159682ed87ca16f7735f50dcde4403dc0c60525f90c756Installer
Complete offline installation with customization
SHA256sum
e06c26b2de306b1f4c12d015daf0b8e72b19672ee26ee2a5f2b86b828477dc1dNetInstaller
All packages are downloaded during installation
SHA256sum
a579fa6c5d1f59819439c8d3ff46fa09e47ed122aa2e77f5c782ba16f8918cfaWeekly
Untested images with the latest updates
SHA256sum
c10ddd7f6cee1de0586fa34a359f8ba7381500efc2587c4d81d2ce7287d5d38bInstaller
Complete offline installation with customization
SHA256sum
5f53a8202fe3edcdee73acfc1f4dcae89b4d91be4708b66fcdd626b259578d66NetInstaller
All packages are downloaded during installation
SHA256sum
e544459861c2f3eb69a6765a7b00847fccda37189307c228a48bd5e37b1f275fWeekly
Untested images with the latest updates
SHA256sum
72558ac80e6ab1c9c8afb6197cbd61101a5c87057c343de5b52abbe028d5ba68Installer
Complete offline installation with customization
SHA256sum
d28fb0441f1fbf7120837b83a1ed8d30a9e645977be1ee9da85293b396ab56eaNetInstaller
All packages are downloaded during installation
Q.)What’s the differences between: Installer? NetInstaller? Weekly? Live?
Q.)How to download Kali Linux images securely?
Want an Updated or Custom Kali Image?
Feeling a little more adventurous? Want to build the latest version of Kali? Want to customize your ISO by adding more tools or change the default settings? Looking for something other than Xfce, GNOME or KDE like Enlightenment, i3mw, LXDE or MATE? Then this is the option for you.
Kali Linux VMware & VirtualBox images are available for users who prefer, or whose specific needs require a virtual machine installation.
These images have the default credentials'kali/kali'.
Virtual Machines DocumentationSHA256sum
de78b3f6e1599987934b04c4c1b002c0bde67822591fef0aaf5191e60eef3025VMware
SHA256sum
1956ab337923095d4213ade006938ac58e3d67b209b9647410e8d85e6eaac409VirtualBox
SHA256sum
06142a974f35436575afb02b903ad1ad2a0416d27395014a0bdc95c385566675VMware
SHA256sum
bf523cd070d47f2b2deff840eba513f5d0bd66d1451163fe65315879423d7590VirtualBox
Vagrant
Vagrant is a tool for building and managing virtual machine environments. With a single configuration file, you can download a base “box” and apply additional configurations like adding an additional network interface, setting the number of CPU cores and memory, or running a script on first boot.
Are you looking for Kali Linux ARM images? We have generated flavours of Kali using the same build infrastructure as the official Kali releases for ARM architecture.
These images have a default credentials of 'kali/kali'.
Kali-ARM Documentation
Raspberry Pi Foundation
SHA256sum
b4aa3d3b405d52fbfae93ddebc58c5845e8d0218fd985401b2158305389a2c08Raspberry Pi 2, 3, 4 and 400 (32-bit)
SHA256sum
5d36fdc4ddf8d27d407ef85a074f6f981c13e0a7abaca859af0c38eea8e8f1f0Raspberry Pi 2 (v1.2), 3, 4 and 400 (64-Bit)
SHA256sum
07af60921a2d4b03a1f74a6895dde8811a1f0a970348948d30d62bc572043aa9Raspberry Pi 1 (Original)
SHA256sum
93462d570e9db553e1c2a8728afe4913f153fb933c1134cc5cb585a80d65bde9Raspberry Pi Zero/Zero W
SHA256sum
01f1aa80be46aac69474041cf4167016383aef740b9a5b1e9c5f164fc5431378Raspberry Pi Zero/Zero W ('Pi-Tail' Edition)
Pine64
SHA256sum
90cb2961253a880e255d793214c96102dccc49ca79019565ec6498c085f02309Pinebook
SHA256sum
5810c4e8462b6c9b65fab25832c169633da6859b1fce89313be3c771c4657626Pinebook Pro
HardKernel
SHA256sum
8d5db7466b47147ebe28cc3ff9cceb98f71a96330d4cf65fbc8be0a1c88ca2f8ODROID-C2
SHA256sum
1cd94374f4a8b5fb4a00aa1c18830134de6f8396efda4407c7fbcf308770459bODROID-XU3
FriendlyARM
SHA256sum
2e935d3cba745a0846e7258bbcc018167d1eb0ddc872b923ab1c9da9dd59d357NanoPi3
SHA256sum
07e481c586f1bd4f98a36fa7f7e6f15b4e23e4ba38fa8aea412b7939e3c740d5
NanoPi NEO Plus2
Banana Pi
SHA256sum
578661cd264b9666f19bee72d4a94aaf772d09c68dbf8fa2d0e0ae1fd168bb46Banana Pi
SHA256sum
a4d8cd5c2a40cebfc54f6f30cdbe828c7f328bf4af50cd5b7ea03dba7c54a018Banana Pro
Gateworks
SHA256sum
338df20b663d81918f3a9ae4104141184f3962b9529256710ab1a85277b083c3Ventana
I.) SHA256SUMS are for the compressed file (*.img.xz)
The Kali NetHunter project is the first Open-source Android penetration testing platform for Android devices, allowing for access to the Kali toolset from various supported Android devices. There are multiple unique features not possible on other hardware platforms.
The Kali NetHunter interface allows you to easily work with complex configuration files through a local web interface. This feature, together with a custom kernel that supports 802.11 wireless injection and preconfigured connect back VPN services, make the Kali NetHunter a formidable network security tool or discrete drop box - with Kali Linux at the tip of your fingers wherever you are!
Statistics
Want to see Kali NetHunter progress? Look at the stats page, to see if your device is supported yet.
Kali NetHunter provides:
- A dedicated NetHunter App, providing a touch screen optimized GUI for common attack categories, such as:
- One-click MANA Evil Access Point setups.
- USB HID Keyboard attacks, much like the Teensy device is able to do.
- BadUSB MITM attacks. Plug in your Kali NetHunter to a victim PC, and have your traffic relayed though it.
- Bluetooth attacks.
- Full Kali Linux toolset, with many tools available via a simple menu system.
- Command line interface to the Kali Linux container.
- Custom, device specific kernel with wireless injection support.
- HDMI output of Kali desktop to external display for supported devices.
- USB Y-cable with the Kali NetHunter kernel - use your OTG cable while still charging your device!
- Software Defined Radio support (SDR). Use Kali NetHunter with your HackRF to explore the wireless radio space.
- NetHunter app store allowing you to grow the potential of Kali NetHunter.
Kali NetHunter Documentation
OnePlus
SHA256sum
753ef16eb45a3f4b46056ed4576f218a3478d1a4955f8e2354b1b7c076685dc7OnePlus One (11)
SHA256sum
84d4b1aaeca98a4fc9e983c457f2b23fd51403bd0546a7dc6c3eb44a4505a159OnePlus 2 (Nougat 5.x)
SHA256sum
157f62048ee8fc9a2e73b5ac993fabc375d168882d2bc8087117e270b5bc2728OnePlus 2 (Pie 9.0)
SHA256sum
7c32304e2eb67cf5cf2f0cbb6c0d2c5910808db7db2c2a6ddbb09401d39b20dfOnePlus 3 (AnyKernel Pie 9.0)
SHA256sum
b3dd27498c0fdef74a5a902772d81de5f1a841cb9a58fafda74e0acb8bafab15OnePlus 3 (AnyKernel 10)
SHA256sum
6c3fcea084a13338b6a6936ddbc620aba6fa97bd2e39e0037ce42f00e10f799bOnePlus 6 (OxygenOS 10)
SHA256sum
c90ae08c24964607fba2aea56e55accbbdf3068dbed8d17c19c6e47acc453b96OnePlus 7 / OnePlus 7 Pro (OxygenOS 10)
SHA256sum
9f27d045a6f95d313a0063eb0a27d51f47ece588363e7f5ff8a0ea008d64f41dOnePlus Nord (11)
Xiaomi
SHA256sum
5954d8dfa4b19ea7b5f39946ed83bae2e4f034bbcc1cb8b4cccee244ceb1cb27Davinci Miui (10)
SHA256sum
75e809978b055c903abc2cb6def3d3f2f868b205ea6cbd23fffa8e6148791b88Xiaomi Mi A3 (LineageOS 18.1)
Nexus
SHA256sum
ce409137e5a361232530afa65e03149657e18ba2734851d77e7e518ea60f1022Nexus 5 (Marshmallow 6.0)
SHA256sum
7e8561ed03335580e1ade882c49287d32bb9538a7a4b31af34224ef28d221de3Nexus 5 (Nougat 5.x)
SHA256sum
3117f601e934ca1432305c13297291e0795199d132ee95a11dd9871c26f4e614Nexus 5X (Oreo 8.0)
SHA256sum
1bed5813db1e81aad4527324662c3effc4d4723315bf1235aa2822c4664caef9Nexus 6 (LineageOS Pie 9.0)
SHA256sum
b1a82321c18e89bc083fccb18f5174126f53ea1725bb8cbeff0d9ba22e8ab01dNexus 6 (Nougat 5.x)
SHA256sum
e203aae021e95fb535f3bc09afb9643619d4726b8323238cd696c4c65cda2f35Nexus 6P (LineageOS 10)
SHA256sum
3d92323c9137508ef71e8cb0da59aea6569a993b251bdb7476d0d041148aa2c2fNexus 6P (Oreo 8.0)
SHA256sum
4a6e901785684ae0b1b128f4956eb66d36737f348f3b1d44207f0ea8502b43e6Nexus 7 2013 (Marshmallow 6.0)
SHA256sum
02601dfe24b3e4725650a100f23dc0fa9687f7d7be49e46292d6072d58729f2dNexus 7 2013 (CyanogenMod Marshmallow 6.0)
SHA256sum
f639e1bbbc0652dc08d9625b22d6a49449a25e5c02be6e549364834d68e669adNexus 9 (Nougat 5.x)
SHA256sum
9e9db3feaa45db26a5d094cc047e5682983752910f19d09ac07012b8ac0a790aNexus 10 (Lollipop)
Samsung
SHA256sum
29da5368ea7d808e86835c90502106b28b15d9faac575d36786d121c501c0f68Samsung Galaxy Tab S4 (LTE) (Oreo 8.0)
SHA256sum
1d1902c7a37a746d72e1b0b96ce8c790229fe715598f6536894d1b72f5fdfa00Samsung Galaxy Tab S4 (WiFi) (Oreo 8.0)
Gemini
SHA256sum
0d2cf313668cecc4ec04888b7acce4ae0adc30332f35cae6b444f89c3a9f5987Gemini PDA (Nougat 5.x)
LG
SHA256sum
87e1909125300248037e6dd9f267122d2eec6c4a0a4151e74c3ed73340f024beLG V20 Int (Nougat 5.x)
Nokia
SHA256sum
1efe4fc74baf75fd60947e0cd55dc7b2fd8cb7b7a928880e952ea32c54fe0e81Nokia 3.1 (Pie 9.0)
SHA256sum
8309f2d704d4dbe0a9340032a860abf1a6c08cf4980ba4080d6574e8a34c9282Nokia 6.1 (11)
Sony XPeria
SHA256sum
9472ef4c373186ca7f0caf3a7f7efb6348c47058e7b3d1cd170174c327a9fb21Sony XPeria Z1 (Marshmallow 6.0)
SHA256sum
e3b5041347a6281d86b84cb40c666c1415760ab1259bfe36ec9f7dc488475982Sony XPeria Z1 (Pie 9.0)
Zerolte
SHA256sum
e161d297082fa3469c7cb612344b37f286a7d9e6342aeeefaf5d6e5fb6ce6d7cZerolte (Nougat 5.x)
ZTE
SHA256sum
33969bd0099755f9b32546ad3b4821f2f43c80e466188968f1da75525572c58bZTE Axon 7 (Marshmallow 6.0)
TicWatch Pro
SHA256sum
16b798bc8c411d912be1eb6f8100855c3237e1ab32d9cfb4b54056714cbe4a2cTicWatch Pro (WearOS Nano)
Generic
SHA256sum
19fd27ed7274d1e1a277bf88560847b3e960182f034f3b853bf999497a6dba5eGeneric ARM64
SHA256sum
5228c79b09accdc087d12adc7a7123ee5c01007ab520c1ec503acca066517b03Generic ARMhf
Kali Cloud images can quickly be deployed in multiple different cloud provider’s infrastructures. This allows easy access to a Kali install in a modern environment with strong hardware resources. These are often used for short term Kali installs that are quick to deploy and quick to tear down.
Kali-Cloud Documentation
Using Container technology such as Docker and LXC/LXD, our Kali containers allow you access to the Kali toolset on your host operating system without the overhead of running an additional full operating system. This does come with limitations, as you won’t have direct hardware access and dealing with inbound connections to tools running in the Kali container can be complicated.
Kali-Containers Documentation
A Kali Linux Live image on a CD/DVD/USB/PXE can allow you to have access to a full bare metal Kali install without needing to alter an already-installed operating system. This allows for quick easy access to the Kali toolset with all the advantages of a bare metal install. There are some drawbacks, as disk operations may slow due to the utilized storage media.
For most users, we recommend the latest “point release” image below, except in cases when a user requires a specific bug patch, in which case the weekly build may be best.
Kali-USB Documentation
SHA256sum
e316b27025922e9f6bca0cacee6dde83dbfd4a549ad18026526f5824af639fc1Kali 2021.3
SHA256sum
438f1bc6409718c0882ef02d19869bf6c8c84ead397c27e3fe3ed23f63591366Weekly Image

SHA256sum
b3e79904c7b50f022cb70ba0f22b1629ab4b84b24001812b7cef2be5d5da4d1aKali 2021.3
SHA256sum
b03a4d79d7815b2aaa4ba1dcf8a7aa5377cc4c98139b60bca70c4483f9dc55c0Weekly Image
SHA256sum
73f4286bba63b68afb2bbe2c5b18949b93ba526404e11b226a2b25146d274b06Kali 2021.3
SHA256sum
f5025482c43afb68801af07d9b00c63b38acb0ee041d6640c6e1a3930bb8bae6Weekly Image
Windows Subsystem for Linux (WSL) is a software package on modern Windows installs that allow you to run Linux alongside your Windows system in an optimized container. The Kali WSL package allows easy access to the Kali toolset. This comes with the same drawbacks of a standard VM, but allows for less overhead and tighter integration with your Windows systems.
WSL DocumentationExperienced penetration testers and security professionals use and trust Kali Linux because we provide full transparency into the build scripts. Feel free to read, investigate, and change build scripts for any images below.
Build Scripts Repository
With Diskinternals VMFS Recovery, you can mount any VMDK file that belongs to any given virtual machine on a server. In order to use the available file access and data recovery tools, you will need to connect to the ESX/ESXi server and mount its disks, partitions and VMDK files. You will be able to repair and open VMDK files and no need in VMDK viewer tool.
Make sure that SSH connectivity is enabled on your ESX/ESXi server. Configure connection settings by entering the IP address of your server, login and password information, and click “Connect”.
How to open VMDK file? There are three different ways to access files after connecting to an ESX (ESXi) server.
Method 1: mounting a *.vmdk disk from a certain Datastore.
Select a folder with the virtual machine being recovered. There, select *.vmdk (or other type) files to mount.
Note: the ESX server does not normally permit low-level disk access to a running virtual machine. With VMFS Recovery, you can still mount the working disk by following the steps described in the how-to guide: Mounting Hard Drives (VMDK files) of a Running Virtual MachineMethod 2: mounting a physical hard drive hosting the ESX (ESXi) server
In this mode, the actual physical hard drive will be mounted, allowing you to access all partitions and unpartitioned areas of the drive. By mounting the physical drive, you’re essentially replicating physical access to the actual hard disk as if it’s been removed from the server and connected directly to your PC.
Method 3: mounting any file from an ESX (ESXi) server
With this method, you can mount any file from an ESX (ESXi) server. This method includes both methods #1 and #2. You can look up Datastore at /vmfs/volumes/. The hard drives are located at /dev/disks/
After selecting the files or drive images to mount, click Mount to add newly mounted disks into the main window.
Diskinternals VMFS Recovery is a tool which makes easy for a user to mount VMDK file on Windows.
Method 4. Mount VMDK disk with 7-Zip
'Unpacking' or mounting VMDK disk is possible with the help of the well-known 7-Zip archiver. This method is quite fast compared to the others and, at the same time, is fairly simple. You just need to right-click on the VMDK file and select “Open Archive”.
You can also try the following method, if this does not suit you.
Method 5. Use Windows Explorer for VMDK disk mounting
You can try to mount VMDK on Windows using built-in tools; Windows Explorer should help you with this.
Here's how to do it: right-click Start and select “Explore”. Now you need to open the folder with the VMDK file using the right mouse button. From the list, select 'Virtual Disk Map'. Next you need to select the drive letter where you intend to mount the VMDK disk. Then click on “OK”.
Method 6. Use VMware Workstation for VMDK disk mounting
VMware Workstation is a desktop program for mounting VMDK on Windows. Just open it, and on the taskbar, select the File tab. Then from the list, select 'Map Virtual Disks ...'. Next, you need to select the drive letter where you want to mount the VMDK file and click OK. Again, this is a simple and efficient method for mounting VMDK on Windows.
Method 7. Try vSphere Disk Development Kit for VMDK disk mounting
You can use vSphere Disk Development Kit to mount VMDK on Windows. This program must be downloaded and installed before use.
Depending on what you want to do, you need to enter certain commands; for example:
- to mount a read-only disk — vmware-mount.exe X: “C:TempTestVM.vmdk”
- to mount several volumes — vmware -mount.exe /v:2 X: 'C:TempTestVM.vmdk'
- to mount the disks for recording - vmware-mount.exe /m:w X: 'C:TempTestVM.vmdk'
- to list all the mounted VMDK disks: vmware-mount.exe /L
A – A physical hard drive of an ESX (ESXi) server connected via method #2. A new partition labeled “data_store_2TB” with VMFS file system appears immediately after mounting the drive. B – A *.vmdk disk from a virtual machine mounted via method #1. Partitions “/” and 'Linux Swap Volume 1” are available immediately after mounting. C – This is just a file connected via method #3. All *.vmdk disks and physical drives of ESX servers can be scanned with any tool included with VMFS Recovery: Recovery mode: NTFS, FAT, Ext2/3/4, VMFS Uneraser and Reader modes: NTFS, FAT, Ext2/3/4, VMFS, Reiser4, ReiserFS, HFS, UFS2, exFAT, ReFS In addition, the mounted *.vmdk disks can be assembled into a RAID array (LDM, Linux RAID).
Related articles
Virtual MachineVirtual DiskVMware/VMDKVirtualBoxHyper-VMount diskNew